in_day_in_life_fin_1.pdf
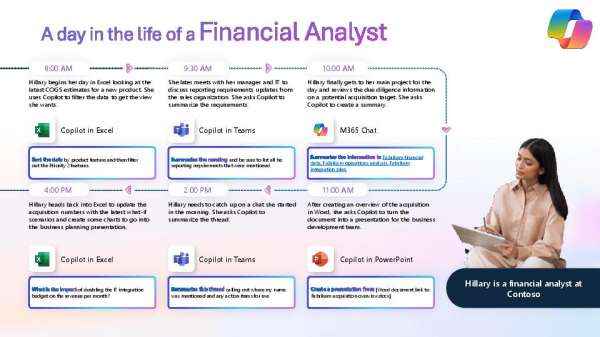
Finance teams often struggle to focus on strategic work due to time-consuming manual tasks. The infographic, "A Day in the Life of a Financial Analyst," showcases how Microsoft 365 Copilot simplifies data analysis, reporting, and stakeholder...










.png?width=306&height=50&name=Logo_width.jpg(2).png)


